CISO as-a-Service to develop Cybersecurity Health Plan
CSA's cybersecurity services help organisations strengthen defences through expert consultancy, funding support, and tailored solutions for different sectors.
On this page
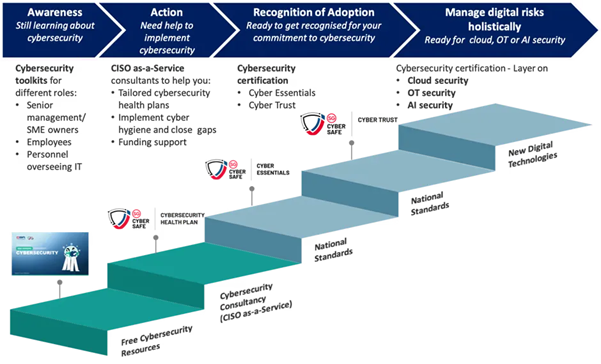
a. Helping organisations with the ‘people’, ‘process’ and ‘technology’ aspects of cybersecurity holistically
An effective strategy for cybersecurity needs to be built on 3 key pillars – “people”, “process” and “technology”. Smaller or less digitalised organisations, such as Small and Medium Enterprises (SMEs) may have limited IT and/or cybersecurity expertise and resources and may find it challenging to implement even baseline cyber hygiene in-house. For those that prefer to tap on 3rd party providers to support them in their cybersecurity implementation, they may consider the following programmes:
Cybersecurity Health Plans delivered by CISO as-a-Service (CISOaaS) cybersecurity consultants – This programme helps organisations with the “people” and “process” pillars of cybersecurity; and
IMDA’s SMEs Go Digital – This programme focuses on pre-approved solutions (for cybersecurity, in this context), and helps organisations with the “technology” pillar of cybersecurity.
Eligible organisations are eligible for funding support when they procure pre-approved solutions under SMEs Go Digital and/or develop a cybersecurity health plan with providers onboarded by CSA. Holistically, these initiatives help organisations to overcome key challenges, such as lack of manpower/resources and lack of budget encountered when implementing cybersecurity.
b. Cybersecurity Health Plan delivered by CISO as-a-Service (CISOaaS) Consultants
1. What you can expect
If you are just getting started in your cybersecurity journey, the cybersecurity consultants (that have been onboarded by CSA) will take on the role to be your “Chief Information Security Officers” (CISO). Such CISO as-a-Service (CISOaaS) providers will
Perform a cyber health “checkup” on your organisation based on the measures in CSA’s Cyber Essentials mark and/or Cyber Trust mark;
Develop a cybersecurity health plan tailored for your organisation;
Help you to close the cyber hygiene gaps identified; and
Prepare your organisation for minimally Cyber Essentials certification.
If you already have implemented good cyber hygiene, or already achieved CSA’s Cyber Essentials mark, you are ready to progress towards adopting a risk-based approach to cybersecurity with CSA’s Cyber Trust mark.
2. Funding support for eligible SMEs
Eligible SMEs can enjoy up to 70% co-funding support when you sign up with the CISOaaS cybersecurity consultants onboarded by CSA.
3. Apply to develop Cybersecurity Health Plan with a CISOaaS Consultant
To sign up for CISOaaS (Cyber Essentials) and/or CISOaaS (Cyber Trust) service with funding support, eligible SMEs may identify its choice of CISOaaS consultant and/or package and sign up for CISOaaS (Cyber Essentials) and/or CISOaaS (Cyber Trust) at IMDA’s CTOaaS portal.
Organisations that are not eligible for funding support but wish to sign up for CISOaaS (Cyber Essentials) and/or CISOaaS (Cyber Trust) service may approach your choice of CISOaaS consultant directly. Please refer to this online listing:
* Please note that CSA does not endorse or recommend any particular organisation, individual, product, process, or service that is linked to the SG Cyber Safe programme, nor can CSA assure the quality of the work of any organisation or individual linked to the SG Cyber Safe programme.
4. Funding support for other organisations
Organisations that are members of the National Council of Social Services (NCSS) should refer to NCSS’s Tech-and-GO! consultancy programme.
5. Other benefits of signing up for CISOaaS providers
Organisations that have successfully completed developing their cybersecurity health plans with their CISOaaS consultants and have appointed a certification body for Cyber Essentials and/or Cyber Trust certification are eligible to be offered scholarships for the Google Cybersecurity Certificate. Please approach your CISOaaS consultant or your appointed certification body for more information.
c. CISOaaS for Health Information Act (HIA) Cybersecurity and Data Security Essentials
1. Whom this is for
This is for all Health Information Act (HIA) entities that are required to meet cybersecurity and data security requirements outlined in the Cybersecurity and Data Security Essentials (CS/DS Essentials). The CS/DS Essentials are developed by MOH in consultation with the Cyber Security Agency of Singapore (CSA), Infocomm Media Development Authority (IMDA) and Personal Data Protection Commission (PDPC) to provide policy clarity on the security measures to be put in place for the proper storage, access, use, and sharing of health information[1].
2. Funding support for eligible SMEs
Eligible SMEs can enjoy up to 70% co-funding support when you sign up with the CISOaaS cybersecurity consultants onboarded by CSA.
3. Apply for CISOaaS consultants to help you meet the Health Information Act (HIA) Cybersecurity and Data Security Essentials
Eligible SMEs may identify its choice of CISOaaS consultant and/or package and sign up at for CISOaaS for CS/DS Essentials for HIA entities and HIMS Vendors at IMDA’s CTOaaS portal.
Organisations that are not eligible for funding support but wish to sign up may approach your choice of CISOaaS consultant directly:
Contfinity Pte Ltd
CISOaaS consultants are progressively being onboarded, and this listing, with relevant pricing information will be updated:
* Please note that CSA does not endorse or recommend any particular organisation, individual, product, process, or service that is linked to the SG Cyber Safe programme, nor can CSA assure the quality of the work of any organisation or individual linked to the SG Cyber Safe programme.
[1] Health information means administrative and clinical information. For the purpose of these CS/DS Essentials, “health information” includes “relevant information” as defined in clause 46(1) of the HIA.
d. Data Protection Officer as-a-Service (DPOaaS)
1. What you can expect
DPOaaS is intended for Social Service Agencies (SSAs) under National Council of Social Service (NCSS):
To meet Data Protection Officer (DPO) obligations under the Personal Data Protection Act (PDPA); and
To implement the prevailing data security measures in the “Data Security Instructions” (DSI) published by the Ministry of Social and Family Development (MSF) Data Governance Office.
Collectively, the CISOaaS (Cyber Essentials) and DPOaaS services help SSAs under NCSS to address the “Data Security Instructions” (DSI) published by MSF Data Governance Office.
2. Funding support
To be updated.
3. Apply for DPOaaS as an add-on to CISOaaS (Cyber Essentials)
For organisations that wish to sign up for CISOaaS (Cyber Essentials) with DPOaaS as an add-on service, please approach your choice of CISOaaS consultant directly - see (b)(iii) above for the "CSA CISOaaS Providers Listing".
e. CISOaaS (Vulnerability Assessment / Penetration Testing (VAPT) Service)
1. What you can expect
Vulnerability Assessment (VA) is a process of identifying, assessing and discovering security vulnerabilities on a computer systems or networks. The systematic approach of identifying, quantifying, and ranking security vulnerabilities enables an organisation to select critical vulnerabilities to resolve based on its available resources and the risks posed.
Penetration Testing (PT) is an authorised and intentional attack on a system to identify vulnerabilities that could be exploited by threat actors. This allows organisations to determine exploitable vulnerabilities in their systems and address them.
Holistically, CISOaaS (VAPT Service) is intended to help organisations, including SSAs, identify exploitable vulnerabilities and prioritise the key vulnerabilities that need to be resolved.
2. Funding support
Eligible SMEs can enjoy up to 70% co-funding support when you sign up for CISOaaS (VAPT Service) with the CISOaaS cybersecurity consultants onboarded by CSA.
3. Apply for CISOaaS (VAPT Service)
To sign up for CISOaaS (VAPT Service) with funding support, eligible SMEs may identify its choice of CISOaaS consultant and/or package and sign up at IMDA’s CTOaaS portal.
Organisations that are not eligible for funding support but wish to sign up for CISOaaS (VAPT Service) may approach your choice of CISOaaS consultant directly. Please refer to this online listing:
• CSA Providers Listing – CISOaaS (VAPT Service) [XLSX, 86 KB]
* Please note that CSA does not endorse or recommend any particular organisation, individual, product, process, or service that is linked to the SG Cyber Safe programme, nor can CSA assure the quality of the work of any organisation or individual linked to the SG Cyber Safe programme.
f. CISOaaS (Incident Response (IR) Service)
1. What you can expect
To complement CISOaaS (Cyber Essentials), which focuses on helping organisations to implement preventive measures for cybersecurity, i.e. pre-incident, organisations may potentially also need help post-incident. The CISOaaS (IR Service) is intended to support organisations that have encountered cybersecurity incident(s).
2. Funding support
Funding support is currently not available for CISOaaS (IR Service).
3. Apply for CISOaaS (IR Service)
For organisations that wish to engage CISOaaS (IR Service), you may approach your choice of CISOaaS (IR Service) provider directly. Please refer to this online listing:
• CSA Providers Listing – CISOaaS (IR Service) Providers
* Please note that CSA does not endorse or recommend any particular organisation, individual, product, process, or service that is linked to the SG Cyber Safe programme, nor can CSA assure the quality of the work of any organisation or individual linked to the SG Cyber Safe programme.
g. Provide feedback about the cybersecurity provider you have engaged that has been onboarded through this programme
Provide feedback about your cybersecurity provider: Feedback form
h. If you are a cybersecurity provider looking to be onboarded by CSA
Sign up to be onboarded as a provider to provide CISOaaS in support of CSA Cyber Essentials and/or Cyber Trust, and adjacent cybersecurity services: Application form
